Privacy concerns from Ledger Live and security concerns from Ledger Connect Kit

What happened?
It's been a rough month for Ledger:
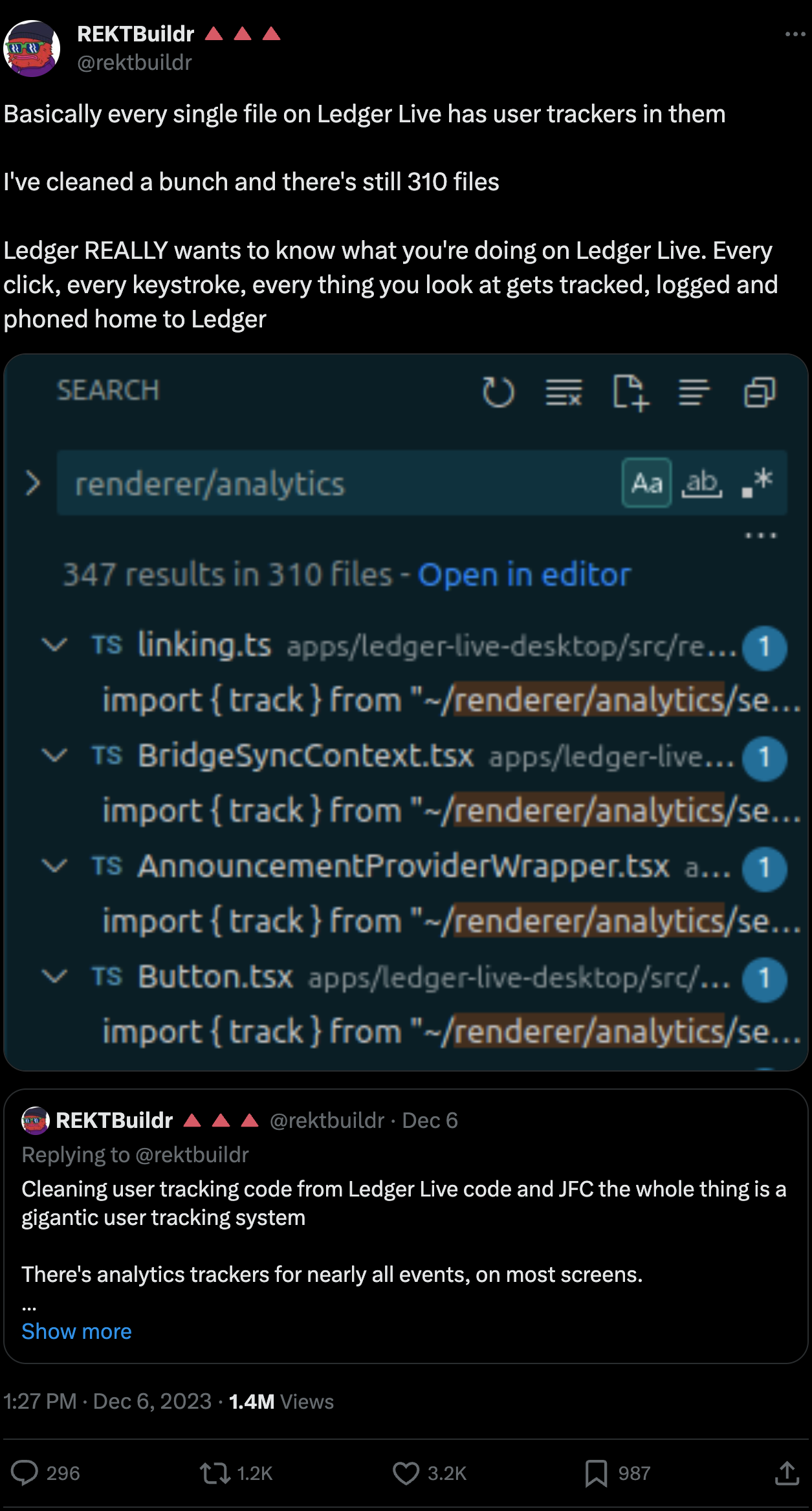
- Someone noticed that Ledger Live sends a ton of user/device data to an outsourced data harvesting service.
- There was an exploit on the Ledger Connect Kit, a Javascript library that implements a button allowing users to connect their Ledger device to third party DApps.
Data Harvesting in Ledger Live
From @rektbuildr's investigation, it looks like Ledger Live is hitting a third-party data collection endpoint (operated by Twilio Segment) to learn as much as possible about user activity - possibly "everything from screen views, to button clicks, error events, installs, uninstalls, etc. It's basically tracking everything. Anything you do on that app gets tracked".
The main question here is why must hardware wallet vendors track their users?
We should be able to use hardware wallets without being tracked and monitored
Hardware wallets should allow incognito operation. The wallet manufacturer does not need to receive an alarm every time you use the thing.
Hardware wallet manufacturers seem to be in the data collection business, not hardware wallet business
That explains why Ledger and Trezor analytics code is built into the core of their apps together with its basic functionality like device installation and update routines?
Analytics would then be the business here and selling hardware wallets is secondary.
Kinda like inkjet printers, the real profit is in selling cartridges. They might as well give the printers away.
I have no idea how anyone thinks it's OK for any of these companies to get an alarm every time you click on a button, open the wallet, access a menu, send a transaction, install a new device and so on. This is crazy!
Just so you're a little extra paranoid, if these apps have analytics all over them and you paste your mnemonic in the wrong place, it's gonna leak your mnemonic to an analytics package. Or worse.....it could "accidentally" leak it when pasted in the correct field as well....who knows, it's sending back a tsunami of data. You can't trust it. It has every menu, every text field, everything in the app wired up to view what you're doing.
The thing is sending everything you do to the manufacturer. You just can't trust it. There should be ZERO phoning back in any of these hardware wallet apps. ZERO. It should not be sending anything out, only IN. When you REQUEST a device install, it sends you a firmware, that is all it should do.
Hardware wallet apps should NEVER send anything OUT.
Unfortunately, Trezor also conducts similar user tracking via Trezor Suite, but it is opt-in, rather than opt-out:
Data Analytics
Anonymous data volunteered by Trezor users directly contributes to improved performance across all the platforms you use Trezor Suite on.
Participation is easy and completely optional. Enable or disable usage data sharing with one click at any time in Trezor Suite Settings. With full control over what you contribute, you can safely take part in making Bitcoin more secure.
TL;DR
- Data is only collected with explicit permission.
- Your sensitive data is not collected.
- We use AWS logging for data analytics and Sentry for error tracking.
- We store the data concerning errors for the period of 90 days.
- Only limited amount of users is able to access the data.
Ledger Connect Kit Exploit
Ledger Connect Kit is a tool that makes it easier for developers to connect DApps to Ledger hardware wallets. These app frontends typically have some sort of a button to connect to the wallet and interact with the smart contract - the Connect Kit is one method of handling that connection.
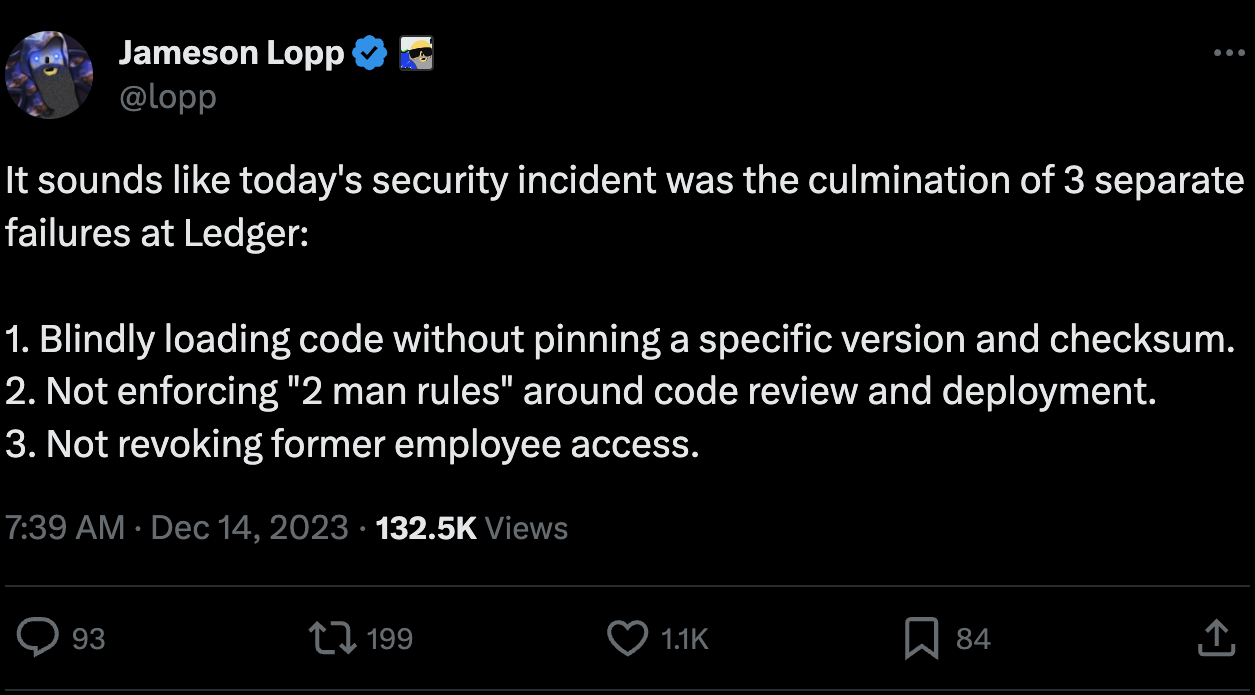
- This morning CET, a former Ledger Employee fell victim to a phishing attack that gained access to their NPMJS account.
- The attacker published a malicious version of the Ledger Connect Kit (affecting versions 1.1.5, 1.1.6, and 1.1.7). The malicious code used a rogue WalletConnect project to reroute funds to a hacker wallet.
- Ledger’s technology and security teams were alerted and a fix was deployed within 40 minutes of Ledger becoming aware. The malicious file was live for around 5 hours, however we believe the window where funds were drained was limited to a period of less than two hours.
- Ledger coordinated with @WalletConnect who quickly disabled the the rogue project.
- The genuine and verified Ledger Connect Kit version 1.1.8 is now propagating and is safe to use.
- For builders who are developing and interacting with the Ledger Connect Kit code: connect-kit development team on the NPM project are now read-only and can’t directly push the NPM package for safety reasons.
- We have internally rotated the secrets to publish on Ledger’s GitHub.
- Developers, please check again that you’re using the latest version, 1.1.8.
- Ledger, along with @Walletconnect and our partners, have reported the bad actor’s wallet address. The address is now visible on @chainalysis. @Tether_to has frozen the bad actor’s USDT.
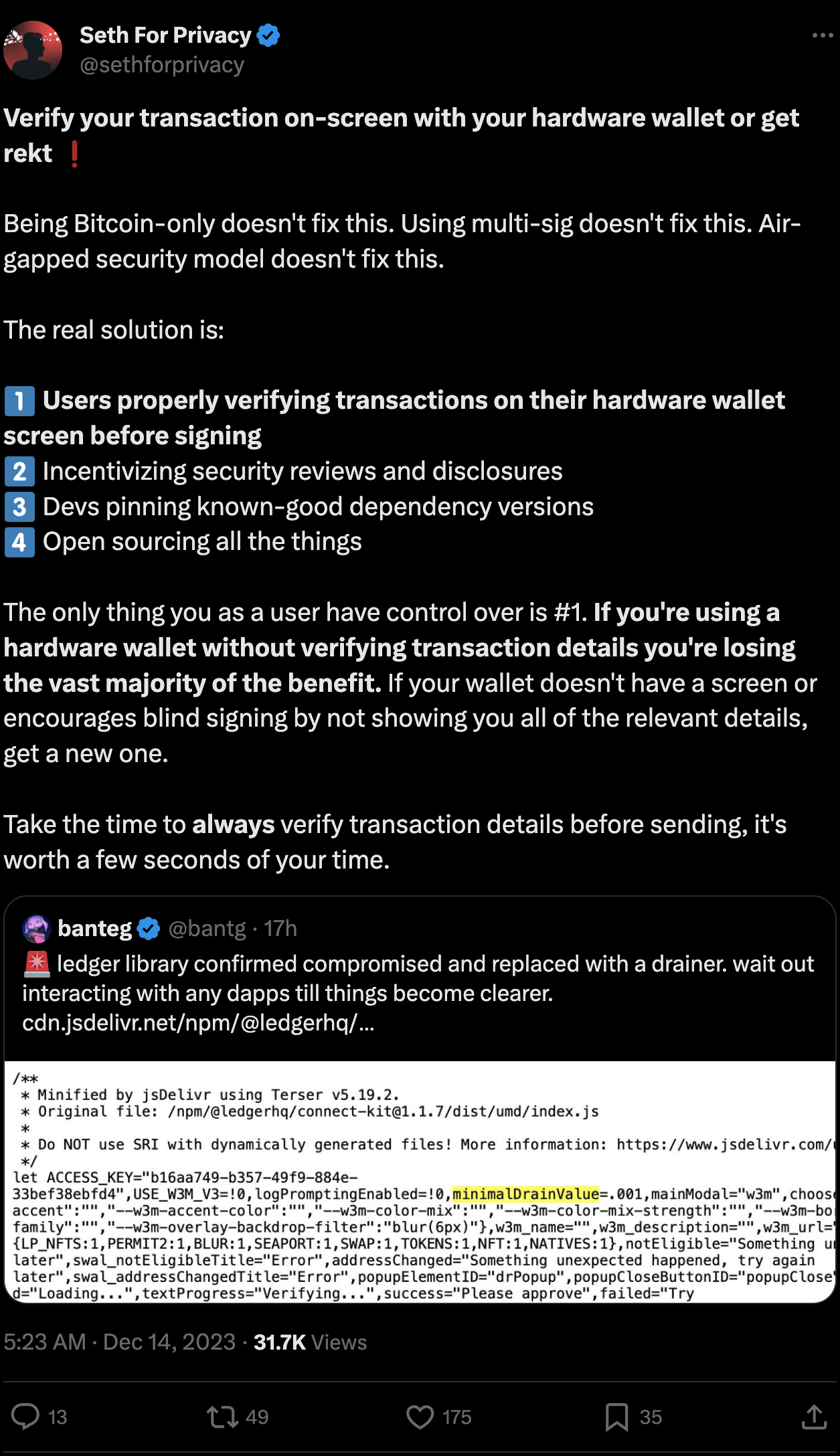
- We remind you to always Clear Sign with your Ledger. What you see on the Ledger screen is what you actually sign. If you still need to blind sign, use an additional Ledger mint wallet or parse your transaction manually.
- We are actively talking with customers whose funds might have been affected, and working proactively to help those individuals at this time.
- We are filing a complaint and working with law enforcement on the investigation to find the attacker.
- We’re studying the exploit in order to avoid further attacks. We believe the attacker’s address where the funds were drained is here:
0x658729879fca881d9526480b82ae00efc54b5c2d
In this particular case, Ledger was able to respond quickly to minimize damage. Interestingly, the malicious version that was draining funds added a class name called DrainerPopup, making it fairly obvious to someone watching the code.
Takeaways
Historically, Ledger has a bad track record for protecting user data and privacy, and the latest exploit also undermines their credibility as security experts.
If you continue to use a Ledger, at least interact with it via some other wallet software than Ledger Live - e.g., Sparrow is a great alternative. Unfortunately, there's still no way to easily update the firmware on a Ledger device without using Ledger Live.
Similarly, if you use a Trezor with Trezor Suite, don't opt in to the data analytics (but you should really just use it with Sparrow instead).
For a bitcoiner wishing to protect their wealth, there are simply better options - take the time to research alternative signing devices (preferably bitcoin-only, like a Coldcard) and review self-custody best practices.