Bitcoin Core Merged BIP-324 and AssumeUTXO Proposals

What happened?
Initial pull requests for BIP-324 and AssumeUTXO have been merged into Bitcoin Core. These upgrades improve node privacy and bootstrapping UX.
BIP-324
BIP-324 is an upgrade to the P2P gossip layer that will allow Bitcoin nodes to communicate with each other over encrypted connections. It is opt-in and backwards compatible (v2 clients will allow inbound v1 connections).
One potential attack vector for nodes on the network is the way nodes communicate with each other via unencrypted traffic. Powerful interests like governments and Internet Service Providers (ISPs) could use this weakness to wage “man in the middle” attacks on Bitcoin nodes, and you wouldn’t know it until it’s too late. Those gatekeepers of internet connections and traffic relays can secretly gather information about sent transactions.
...
BIP324 is an improvement proposal that aims to enhance the privacy of Bitcoin nodes, making the network more robust and secure. The update is a proposal to encrypt traffic between nodes connected to the Bitcoin network to make network metadata, like the location a transaction is coming from, more private, making it harder for third parties monitoring internet traffic to spy on this type of data transfer.
How BIP324 helps improve node privacy:
- Encrypted communication: By encrypting the messages exchanged between nodes, BIP324 makes it much harder for eavesdroppers to intercept and analyse the data transmitted between nodes, protecting user privacy.
- Authentication: The Noise protocol also ensures that the nodes communicating with each other are authentic, preventing potential man-in-the-middle attacks.
- IP address protection: Since the communication between nodes is encrypted, it becomes more difficult for malicious actors to associate a user’s IP address with their transactions or other activities.
- Confidentiality against passive attacks: A passive attacker having recorded a v2 P2P bytestream (without timing and fragmentation information) must not be able to determine the plaintext being exchanged by the nodes.
- Observability of active attacks: A session ID identifying the encrypted channel uniquely is derived deterministically from a Diffie-Hellman negotiation. An active man-in-the-middle attacker is forced to incur a risk of being detected as peer operators can compare session IDs manually, or using optional authentication methods possibly introduced in future protocol versions.
- Pseudorandom bytestream: A passive attacker having recorded a v2 P2P bytestream (without timing information and fragmentation information) must not be able to distinguish it from a uniformly random bytestream.
- Shapable bytestream: It should be possible to shape the bytestream to increase resistance to traffic analysis (for example, to conceal block propagation), or censorship avoidance.
- Forward secrecy: An eavesdropping attacker who compromises a peer’s sessions secrets should not be able to decrypt past session traffic, except for the latest few packets.
- Upgradability: The proposal provides an upgrade path using transport versioning which can be used to add features like authentication, PQC handshake upgrade, etc. in the future.
- Compatibility: v2 clients will allow inbound v1 connections to minimise risk of network partitions.
- Low overhead: introducing a new P2P transport protocol should not substantially increase computational cost or bandwidth for nodes that implement it, compared to the current protocol.
AssumeUTXO
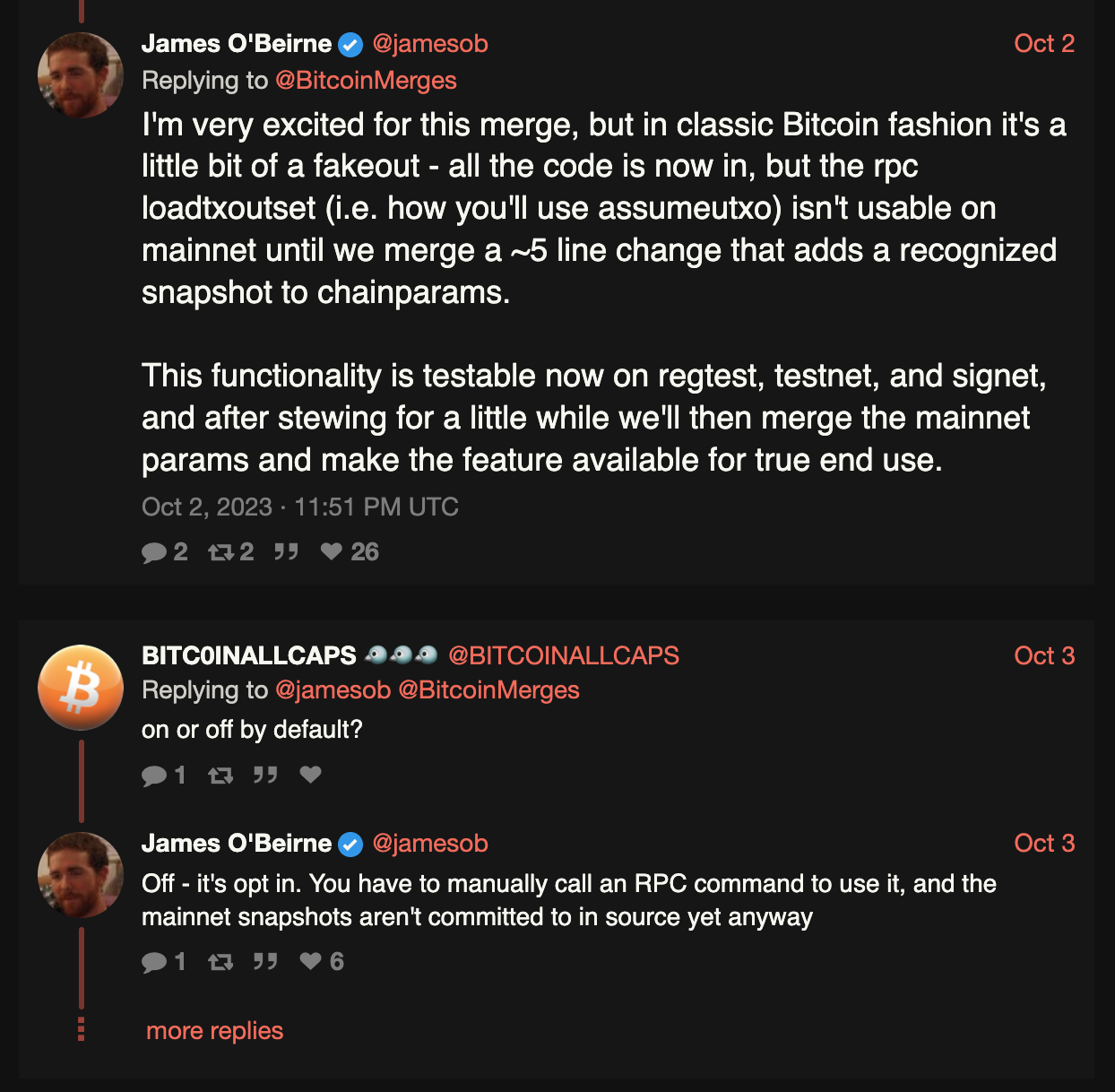
AssumeUXTO enables instant UTXO set bootstrapping for Bitcoin nodes by temporarily trusting a snapshot from another node (while still downloading and verifying the entire chain in the background).
AssumeUTXO is a proposed, optional setting that would allow users to make use of their Bitcoin node before initial block download (IBD) is complete. IBD is one of the most prohibitive costs to running a node, so reducing or hiding this burden is an important improvement for Bitcoin’s usability and decentralization.
AssumeUTXO allows users who are launching full nodes to first download a full copy of the UTXO set from a node, allowing their node to immediately start crafting, querying, and broadcasting transactions. In the background, the full node still downloads and verifies each block, maintaining the trustless nature of Bitcoin.
Without AssumeUTXO, users must wait to craft and query transactions until their node has downloaded and validated the entire blockchain, a process that can take up to two weeks depending on the computer.
More Resources
- BIP-324
- BIP-324: Version 2 P2P Encrypted Transport Protocol
- Version 2 P2P transport | Bitcoin Optech
- BIP324: Improving Bitcoin’s P2P Transport Protocol - YouTube
- What Is BIP324? - The Bitcoin Manual
- BIP 0324 - Bitcoin Wiki
- Marty's Bent 1231: BIP 324 would bring encryption to bitcoin's P2P layer and it needs some review
- BIP-324: A Message Transport Protocol That Could Protect Bitcoin Peers
- AssumeUTXO